W Instytucji Specjalistycznej VS DATA powołaliśmy zespół Szybkiego Reagowania dedykowany do obsługi incydentów naruszenia bezpieczeństwa systemów informatycznych.
Oferta
Obsługa incydentów
Jak działamy?
Obsługa cyber incydentu odnosi się do działań podejmowanych przez organizację w odpowiedzi na podejrzenie lub wykrycie naruszenia bezpieczeństwa IT. Decydując się na współpracę z nami masz gwarancję poufności, doświadczenia i szybkiej reakcji na zaistniałą sytuację.
Poniżej przedstawiamy kroki, które podejmujemy wraz z klientem w odpowiedzi na cyber incydent:
1
Przygotowanie
- Tworzymy plan reagowania na incydent
- Organizujemy zespół odpowiedzialny za reagowanie na incydent
- Zapewniamy odpowiednie narzędzia i zasoby do zabezpieczenia danych, analizy powłamaniowej i odbudowania infrastruktury
2
Weryfikacja i zabezpieczanie danych
- Zbieramy wszystkie dostępne informacje na temat zaistniałego incydentu
- Określamy zakres i wpływ incydentu
- Izolujemy i zawężamy obszar zagrożenia, aby zapobiec dalszemu rozprzestrzenianiu się problemu
- Zabezpieczamy dowody na potrzeby śledztwa
3
Komunikacja
- Przygotowujemy plan komunikacji wewnętrznej i zewnętrznej
- Informujemy kierownictwo i inne zainteresowane strony o incydencie i podjętych działaniach
- Opracowujemy zgłoszenie wstępne (później również uzupełniające) do Urzędu Ochrony Danych Osobowych
- Pomagamy w kontakcie z organami ścigania
4
Analiza powłamaniowa
- Dokładnie przeanalizujemy incydent, aby zrozumieć jego przyczyny i skutki
- Ustalimy pacjenta zero oraz przebieg ataku
- Określimy czy doszło do wycieku danych (eksfiltracji)
- Przekażemy działowi IT wskaźniki kompromitacji (IoC)
5
Usunięcie i odbudowa możliwości operacyjnych
- Podejmujemy z Klientem działania naprawcze w celu eliminacji zagrożenia
- Przywracamy normalne działanie usług i systemów
- Wdrażamy wszelkie konieczne poprawki, aby uniknąć powtórzenia incydentu
- Określamy, jakie wnioski z incydentu można wyciągnąć i jakie poprawki można wprowadzić w procedurach oraz infrastrukturze
6
Raport i rekomendacje
- Opracowujemy raport z analizy powłamaniowej
- Opiszemy wszystkie działania podjęte w odpowiedzi na incydent
- Przygotowujemy rekomendacje po incydencie zwiększające odporność organizacji na przyszłe cyber incydenty
Każdy cyber incydent jest inny, więc powyższe kroki mogą wymagać dostosowania do konkretnej organizacji i zastanej sytuacji. Ważne jest, aby zaatakowana organizacja reagowała w sposób szybki przy jednoczesnym zastosowaniu najlepszych praktyk i metodyk obsługi incydentów IT.
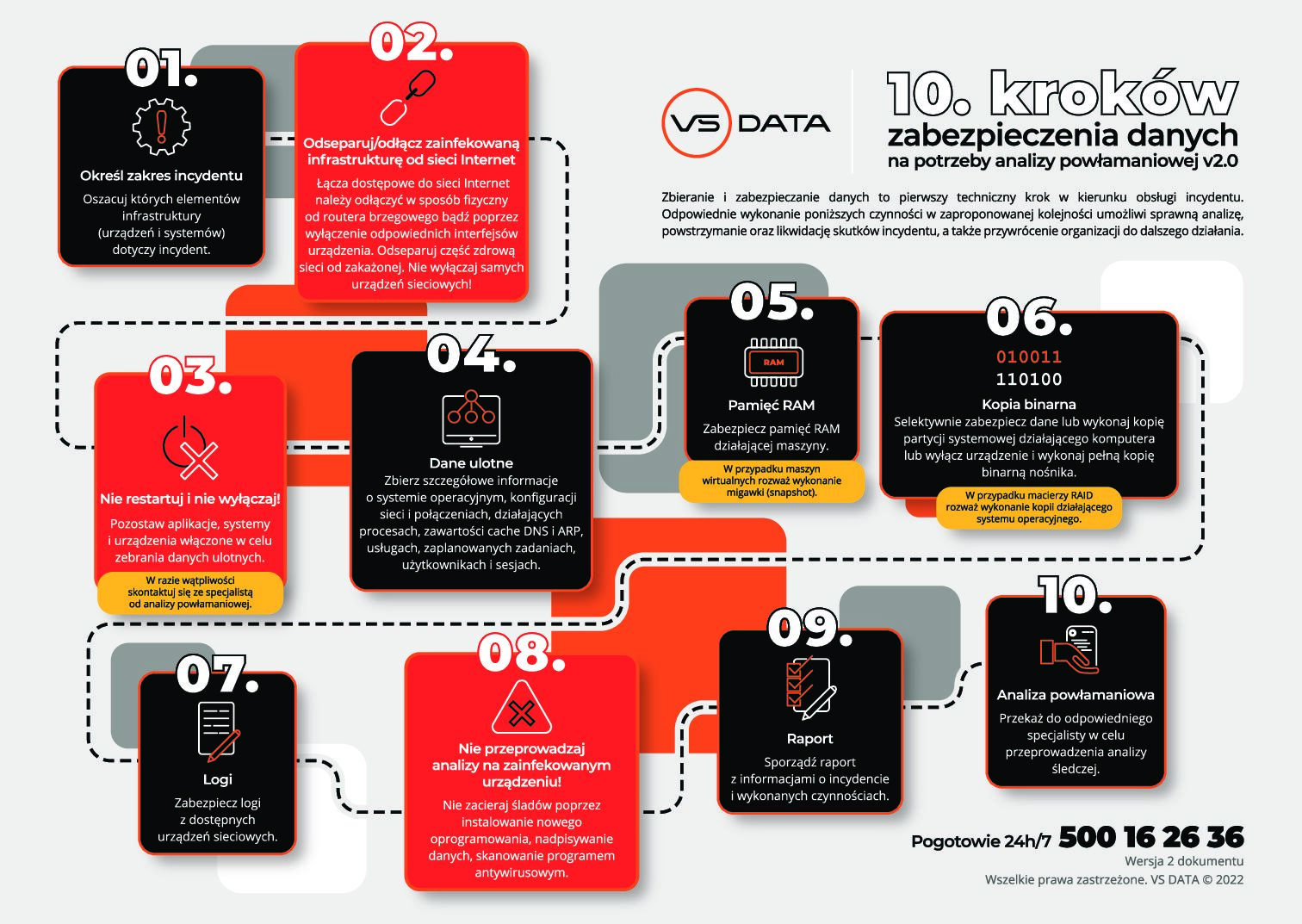
W celu poprawnej obsługi incydentu i wykonania analizy powłamaniowej niezbędne jest przeprowadzenie poprawnego procesu zabezpieczania danych. Poniżej przedstawiamy grafikę systematyzująca wykonywane przez specjalistów ds. reagowania na incydenty czynności.
Kontakt z nami: [email protected], tel. +48 500 16 26 36
Grafika przedstawia 10 kroków zabezpieczenia danych na potrzeby analizy powłamaniowej.
Do pobrania
SSC 800-61 National Cybersecurity Standard:
Handbook for Handling Computer Security Incidents (October 2021).
Skontaktuj się z nami
Nasze doświadczenie w obsłudze incydentów gwarantuje Państwu zwiększenie bezpieczeństwa systemów informatycznych w Państwa firmie.
Zadzwoń!
500 16 26 36
NAPISZ
[email protected]
DOŚWIADCZENIE
Odzyskujemy dane dla klientów prywatnych, firm i instytucji państwowych.
15
6000
1000000
5
Zaufali nam:


